FAV/E - Find A Vulnerability/Exposure
To be a successful bug bounty hunter, you must be on a continuous search for new vulnerabilities and exploits. Aside from staying glued to #infosec Twitter feeds, one of the best ways of introducing yourself to new vulnerabilities and exploitation methods is to stay up to date with the latest CVEs. Normally to search for CVEs I would open a new tab in the browser, search Google for the technology in question and go down the rabbit hole, sometimes eventually finding a CVE. This long drawn out process gets repetitive fast, and I wanted a tool similar to SearchSploit that would allow me to search for CVEs fast while using only the CLI.
Why Re-Invent the Wheel?
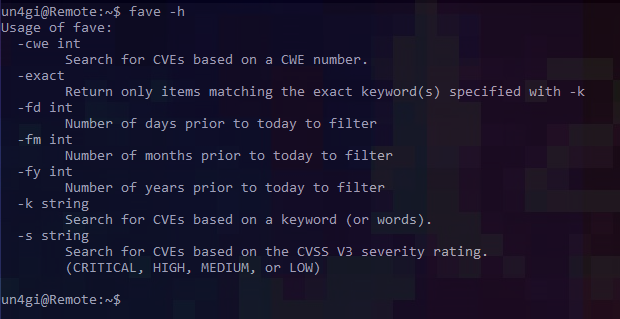
Anyone who has ever used SearchSploit knows just how valuable the tool can be. While it’s a great tool for network penetration tests or for making very specific queries, I needed something a little more flexible. The goal of FAV/E was to create a tool that could query the NIST CVE database using various filters that would enable its future integration into my automation pipeline. Let’s take a look at the options FAV/E has for filtering results:
As shown above, FAV/E allows you to filter results based on various traits. One of the main features I wanted to integrate was the ability to display only new CVEs. What constitutes a “new” CVE? I’ll let you decide! The fd, fm, and fy flags can all be used to filter results based on a number of days, months, and/or years respectively.
As you can see above, I supplied the ”-fy” flag with a value of 1 to search for any CVEs matching the keyword (-k) ”un4gi”. As a result, any of the CVEs assigned to me within the past year were displayed. Conversely, in the second image I supplied a filter ”-fm 6” to show any CVEs containing the same keyword. Sadly, I have had no CVEs assigned within the past six months so no results were displayed (I do have some pending - stay tuned!).
Aside from filtering by date and/or keywords, FAV/E provides the option of filtering by CWE number and CVSS severity through use of the ”-cwe” and ”-s” flags respectively.
As shown above, the image on the right shows filtering for only XSS (CWE 79) CVEs published or modified within the last 7 days. The image on the left shows a search for both Critical and High severity vulnerabilities with CVEs published or modified within the last 7 days. As you can see, these flags can be combined with any of the other filters to narrow down the results to be as specific as you would like.
Through the creation of FAV/E, I have already noticed an improvement in my workflow and am looking forward to integrating its functionality into my automation pipeline. If you’d like to try out the tool, you can check it out on Github using the button above. I am always open to suggestions, so please let me know if you have any comments, questions, or suggestions on how I can improve the tool! I look forward to hearing feedback from the community!